case study |
 |
 Cybercrime is big business in the United States. In fact, according to the Federal Bureau of Investigations, cybercriminals make between $5,000 to $65,000 a month doing everything from stealing and selling credit-card numbers to committing identity fraud. Unfortunately, the crimes - and criminals - are rarely visible to the naked eye. And because the offenses aren't nearly as life threatening as physical assault or headline making as bank robbery, it's relatively easy to forget about the severity of the threat. But it's that widespread ignorance upon which cybercriminals prey. Cybercrime is big business in the United States. In fact, according to the Federal Bureau of Investigations, cybercriminals make between $5,000 to $65,000 a month doing everything from stealing and selling credit-card numbers to committing identity fraud. Unfortunately, the crimes - and criminals - are rarely visible to the naked eye. And because the offenses aren't nearly as life threatening as physical assault or headline making as bank robbery, it's relatively easy to forget about the severity of the threat. But it's that widespread ignorance upon which cybercriminals prey.
Of the 303,809 complaints received in 2010 by the Internet Crime Complaint Center (a partnership among the FBI, National White Collar Crime Center, and the Bureau of Justice Assistance), more than 120,000 were referred to law enforcement for investigation. And of those, the top five crimes included nondelivery of payment/merchandise, identity
theft, auction fraud, credit-card fraud, and miscellaneous fraud (e.g., e-mails requesting bank numbers to wire money on behalf of a deposed prince). What's more, every person who uses the Internet is a potential victim, which, according to a December 2010 survey conducted by the Pew Internet & American Life Project, is approximately 77 percent of the U.S. population.
 |
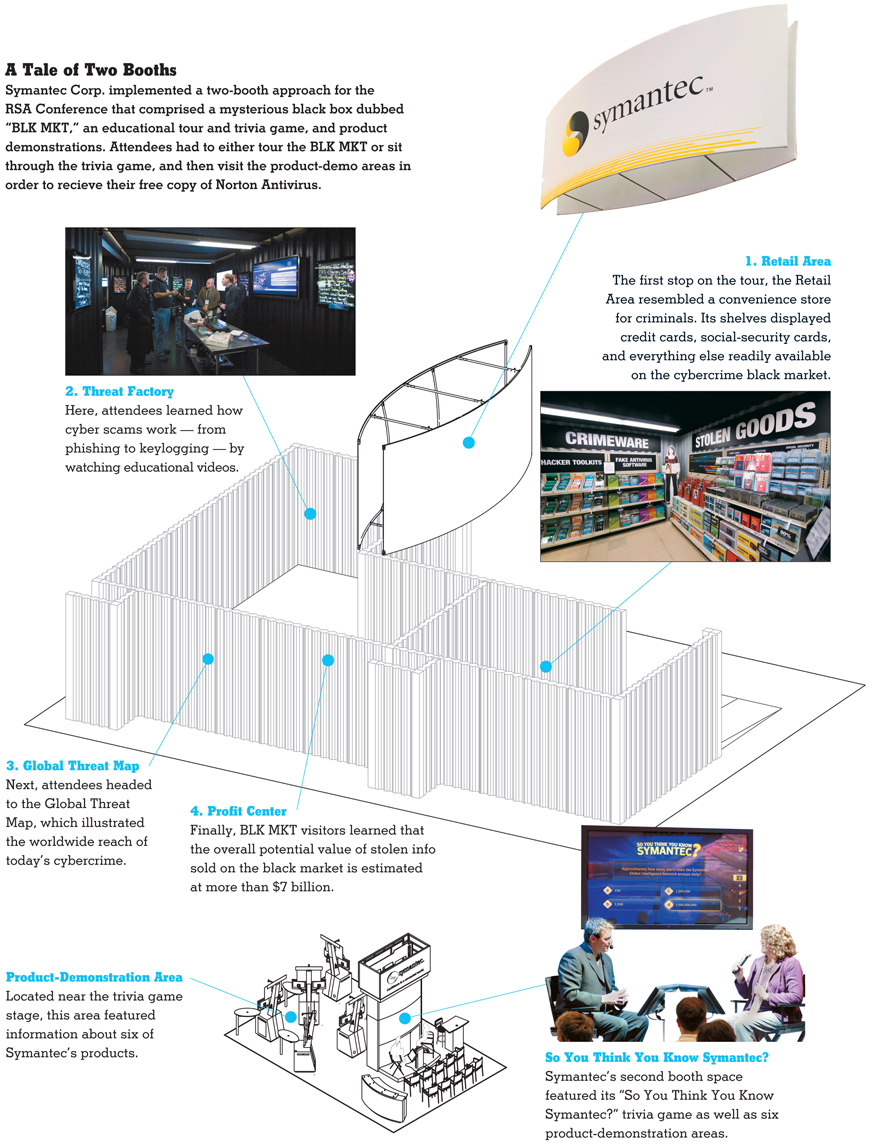
| Symantec Corp. staffers led attendees
through the the BLK MKT,
a large, black enclosed structure. |
Fortunately, most consumers and corporations protect their information and identities through various measures, including firewalls, data encryption, antivirus software, antispyware technology, and plain-old common sense. And though there is no fail-safe way to guarantee your data and identity will be protected, just being aware of the risk puts you one step ahead of the cybercriminals.
Given the omnipresent threat from computer hackers and other digital deviants, Symantec Corp., best known for its Norton suite of antivirus and security software, was surprised to discover that attendees weren't that interested in its exhibit at the RSA Conference - the largest information-security conference in the country. "We felt that as the industry leader in security, attendees would want to come into our booth to learn about our new technologies, products, and services," says Michele Stankevich, marketing programs manager at
Mountain View, CA-based Symantec.
But at the 2009 show, staffers informed Stankevich that attendees weren't heading to Symantec in droves, nor were they spending much more than a minute or so in the booth when they did make the effort to breach the aisle carpet. "We realized that attendees were walking past our booth because they thought they already knew everything about us," she says. To attendees, Symantec was the Tom Hanks of the IT-security industry - well known and universally appealing, but terribly vanilla and not really worth further investigation. After all, once you've seen one Hanks movie, you've seen them all. So if Symantec wanted to titillate attendees at RSA, it needed to channel James Franco - sexy, mysterious, and unconventional.
In preparation for RSA 2010, which was held in San Francisco, Stankevich searched for something that would intrigue attendees enough to step foot into Symantec's exhibit to learn about all of its product offerings. Luckily, she didn't have to look far. Symantec's advertising agency, Leo Burnett Worldwide, had designed just what Stankevich was looking for a few months prior, but in the form of a road show marketing campaign for the company's consumer-business unit. Dubbed the "BLK MKT" (pronounced "black market"), the main attraction of the road show was a black 30-by-40-foot structure. That structure, fabricated by Chicago-based Exhibit Concepts Inc., housed various rooms illustrating different aspects of the cybercrime world, from the type of information that can be stolen to the ways in which criminals steal it. And while the consumer-business unit used the BLK MKT to provide employee education about the Norton suite of products via informational tours at various Symantec offices across the United States, Stankevich reasoned that with a little tweaking, she could make the BLK MKT suit the needs of the RSA audience - and Symantec management agreed.

With the green light from the consumer-business unit and upper management, Stankevich and Symantec's corporate events team members sequestered the BLK MKT and began retooling it, starting with the tour script. "Since most RSA attendees are IT-security professionals specializing in enterprise computing, we had to shift the focus of the tour," Stankevich says. So instead of extolling the benefits of Norton to Symantec's own sales staff, Stankevich would revamp the BLK MKT to further explore the inner workings of cybercrime - and convey the continued threat to RSA attendees. "It was our responsibility to let attendees know the security threat is still very real, and that Symantec offers solutions to thwart such cyberattacks," she says.
In addition to the BLK MKT, Stankevich and her team devised another activity to keep attendees' attention and challenge attendees' belief that they already knew everything there was to know about the company. A trivia game dubbed "So You Think You Know Symantec?" that would share a separate exhibit space with various product-demo stations across the aisle. Featuring a handful of questions about Symantec and its products, the game would be one part fun, engaging activity, and one part educational experience. What's more, the trivia game would serve as an alternative option for booth visitors that didn't want to participate in the BLK MKT tour (whether due to time constraints or lack of interest).
 To tie together the seemingly disparate BLK MKT tour, trivia game, and product-demo areas that comprised Symantec's exhibit strategy, Stankevich added more conventional tactics to the mix: a passport component (attendees would receive a game card on which stamps would be placed after they visited both exhibits), premium giveaways, and big-ticket prize items, all of which were introduced via a pre-show marketing campaign that began two months prior to the March show. To tie together the seemingly disparate BLK MKT tour, trivia game, and product-demo areas that comprised Symantec's exhibit strategy, Stankevich added more conventional tactics to the mix: a passport component (attendees would receive a game card on which stamps would be placed after they visited both exhibits), premium giveaways, and big-ticket prize items, all of which were introduced via a pre-show marketing campaign that began two months prior to the March show.

In January, Symantec launched a microsite that featured its session schedule, keynote, info about the BLK MKT exhibit and game, and a code redeemable for a complimentary exhibit-hall pass. The microsite also mentioned a magical phrase for RSA attendees - "earn a free copy of Norton 2010 software." "Though Norton is a consumer product and not really applicable to corporate IT-security, it's still a highly sought-after item," Stankevich says. "We knew attendees would want it."
Following the launch of the microsite, Symantec sent an e-blast to the show's pre-registered attendees. Stankevich kept the e-blast simple, including little more than the BLK MKT logo on a black background, the company's two booth numbers (1416 for the BLK MKT, 1426 for the game and product-demo areas), and the text: "You're about to experience information superhighway robbery."
In addition to the microsite and e-blast, Stankevich planned an on-site marketing move: a bag drop. The postcard bag drop was reminiscent of the e-blast - black background with white text. This time, however, the message was a little more unsettling: "91% of corporate records compromised in 2008 were targeted by organized crime." The intent of the stat wasn't to send IT-security professionals running to reinforce their firewalls, but rather to stop them cold in their tracks. "We wanted to hit them with a statistic that would make them think twice about their own security measures," she says.
The reverse of the card featured an invitation to visit the exhibits. Additional text outlined Symantec's security-related conference sessions, the time of its keynote, and a list of products that would be demonstrated in the booth, including its Control Compliance Suite, Hosted Services, Data-Loss Prevention Suite, Security Management/Workflow, and the Symantec Protection Suite. What's more, the card mentioned the Norton giveaway with instructions on how attendees could get their hands on a free copy: "Be sure to stop by the Symantec booths 1416 and 1426 to pick up a game card, check out our booths, and earn a free copy of
Norton 2010 software."

Though the Norton freebie would surely be enough to get people to stop by the exhibit, the company's ultimate intention was to lure unassuming attendees into the dark world of the cybercrime black market - and keep them there long enough to learn about Symantec products.

When the show floor opened and attendees arrived at booth 1416, they encountered the imposing BLK MKT structure. Made of the same corrugated steel used to make large shipping containers, the BLK MKT looked like something pulled straight off the docks. And as attendees queued up, grabbed a passport card, and waited to have their badges scanned by a Symantec staffer standing behind a counter, they could only wonder what lurked inside the black box.
Approximately every 15 minutes, a Symantec staffer, acting as a tour guide, invited groups of about 12 attendees to enter the BLK MKT, saying, "Welcome to the Internet black market - where cybercriminals buy, sell, barter, and trade you."
As the group entered the BLK MKT, they encountered the Retail Area, which was set up to resemble a store environment. The shelves were lined with everything a cybercriminal would need to commit identity theft, hack into computer systems, etc. For example, one wall of the crime shop featured fake antivirus software and "hacker toolkits" (software programs purposely written to probe a victim's computer and automatically exploit security holes). Another wall showcased a smorgasbord of stolen credit cards, social-security cards, drivers licenses, etc., each conveniently packaged and ready to be bought and sold on the black market. The cards, kits, and software for "sale" in the BLK MKT illustrated the fact that buying and selling identities was just as easy as walking into a gas station and snapping into a Slim Jim.
 As alarmed attendees perused the wealth of pilfered personal information and illegal software lining the walls, the guide explained, "The items you see on display here represent what's readily available in the underground economy. Want to buy some malicious code and use it to steal credit cards? Or maybe you're looking for a new identity so you can impersonate someone else for financial gain. You've come to the right place." And with all the unbridled enthusiasm of a Walmart greeter, the guide ushered the group through a false door that led to the next stop on the tawdry tour: the Threat Factory. As alarmed attendees perused the wealth of pilfered personal information and illegal software lining the walls, the guide explained, "The items you see on display here represent what's readily available in the underground economy. Want to buy some malicious code and use it to steal credit cards? Or maybe you're looking for a new identity so you can impersonate someone else for financial gain. You've come to the right place." And with all the unbridled enthusiasm of a Walmart greeter, the guide ushered the group through a false door that led to the next stop on the tawdry tour: the Threat Factory.

"Welcome to the Threat Factory," announced the guide. "Here, you'll get a unique look at online threats from the criminal's perspective. You'll see how their scams are created, tested, distributed, and tracked." While inside the Threat Factory, attendees viewed four videos demonstrating various tools and tactics used by cybercriminals. For example, one video described "keylogging," a practice of covertly and remotely recording the keys struck on your keyboard. The malicious software sends the key logs to a server where the information is then collected. To bring the threat home, the guide explained to the group, "If one of your employees gets infected, their name, IP address, log-ins, and passwords can all be snatched in a flash."
The subsequent videos highlighted phishing scams (in which cybercriminals create websites that replicate legit sites such as banks and other financial institutions to get personal information), fake antivirus software offers (in which a phony alert pops up on a user's computer, informing him or her of malware and directing the user to a third-party site to purchase and download faux software), and the use of bots (a type of malware that allows an attacker to remotely take control over an infected computer).
Each video demo included an explanation of the threat and an example of how each is deployed for an up-close-and-personal look inside an otherwise unknown world. This sneak peak into the underbelly of cybercrime was to IT-security pros what walking through the wardrobe into Narnia was to the Pevensie brood: fantastic, curious, and scary.

As uneasiness no doubt settled under attendees' skin, they made their way to the Malware Testing Station. Here, visitors learned how easy it is for hackers to test and rewrite malicious code - constantly updating it so it slips by security software undetected. Additional demos in the Threat Factory illustrated how cybercriminals use their own secret language to communicate on instant-message boards to buy and sell malicious code, stolen credit-card
numbers, identities, and hacker toolkits.
After watching the videos, attendees moved on to the Global Threat Map,
a 50-inch wall-mounted flatscreen monitor that displayed a world map. The map showed the digital path cybercriminals leave behind as they carry out their attacks. "Once a cybercriminal implements or sells his malicious code, its global path of destruction can be tracked and collected based on their exploits by time, country, industry, IP address, and other parameters," explained the guide, who went on to say that most cybercriminals have found a way to cover their tracks.
The brazen cybercrime activities are motivated by one thing: cold, hard, cash. To illustrate that point for attendees, the guide took them to the BLK MKT's Profit Center. Here, visitors learned that between 2007 and 2008, Symantec valued advertised stolen goods for sale at more than $276
million - with credit-card info comprising 32 percent of that cache. In fact, the potential value of credit-card data sold on the black market is more than $7 billion. "As criminal career choices go, online crime is fairly low risk and highly rewarding," the tour guide informed attendees.
|
 |
After learning the financial side of the business, attendees headed to the final section of the BLK MKT, where the guide presented information about the top scams and scammers currently
active - and stats about the future of the cybercrime industry. "We could see more than 15 million unique malware samples by the end of 2010. Every day brings newly developed cyber schemes designed solely to take advantage of security weaknesses and rip off your organizations with such stealth that most victims don't even know they've been attacked."
Well, crap. If cybercrime is everywhere, stolen identities are as easy to come by as a bag of Corn Nuts and a Diet Coke, hackers can conceal their tracks, and business is booming, then what can the IT-security industry
possibly do to protect its wares?
Conveniently, Symantec had the answer after the tour through the BLK MKT. "If you're interested in learning
more about what you can do to better
protect your employees and your business assets from cybercriminals," said the guide, "talk to one of our security experts." And with that, attendees received a stamp on their passport cards and were directed to Symantec's second booth space, which featured the six product-demo stations and the "So You Think You Know Symantec?" presentation area.
 Here, staffers invited interested booth visitors to drop their business cards into a fish bowl and grab a seat in a small presentation space to watch the show, which took place several times throughout the day. Featuring a raised platform, two black director's
chairs, and a 52-inch flatscreen monitor mounted to a white back wall, the aisle-side trivia game area caught the attention of passersby, who often congregated in the aisle to enjoy the show. Before the host took the stage, he drew a name from the bowl, and that person was beckoned to take a seat on stage with him to play the game. After answering several questions about Symantec and its products, the contestant received a prize (a Nintendo Wii console, Flip camera, GPS unit, or a set of Bose headphones) based on the number of correct answers he or she provided. Those that watched the trivia game received a stamp on their passport card and were invited to visit the BLK MKT (if they hadn't yet) or head over to the product-demo areas. By either touring the BLK MKT or sitting through the game and then visiting one of the six demo stations, attendees obtained the passport stamps necessary to receive their free copy of Norton AntiVirus. Here, staffers invited interested booth visitors to drop their business cards into a fish bowl and grab a seat in a small presentation space to watch the show, which took place several times throughout the day. Featuring a raised platform, two black director's
chairs, and a 52-inch flatscreen monitor mounted to a white back wall, the aisle-side trivia game area caught the attention of passersby, who often congregated in the aisle to enjoy the show. Before the host took the stage, he drew a name from the bowl, and that person was beckoned to take a seat on stage with him to play the game. After answering several questions about Symantec and its products, the contestant received a prize (a Nintendo Wii console, Flip camera, GPS unit, or a set of Bose headphones) based on the number of correct answers he or she provided. Those that watched the trivia game received a stamp on their passport card and were invited to visit the BLK MKT (if they hadn't yet) or head over to the product-demo areas. By either touring the BLK MKT or sitting through the game and then visiting one of the six demo stations, attendees obtained the passport stamps necessary to receive their free copy of Norton AntiVirus.

When the BLK MKT finally shut its doors, 519 attendees (including five industry analysts) had made their way through the experience, 288 people participated in the trivia game, and Symantec gave away hundreds of copies of Norton AntiVirus. But beyond those results, the BLK MKT received accolades from a plethora of media outlets, including CNET, PC Magazine, the San Francisco Examiner, and industry blogs such as Tech Blog, Nerd Rage, and AntiVirus News.
"The positive feedback from attendees, customers, our booth staff, and the media showed us we had met our challenge of making people more aware of the latest security solutions Symantec has to offer," Stankevich says. "The BLK MKT was definitely worth the commitment and hard work we put into it." That effort is no doubt what led to another coup for Stankevich and her team - kudos from reps for the United States Strategic Command, a government organization that is charged with protecting U.S. cyberspace. "They liked our video demos so much that they asked us for copies so they could use them to train their internal employees," she says.
In the end, the BLK MKT kept IT-security professionals engaged and in Symantec's exhibit for more than 15 minutes, the trivia game educated attendees about the company, and the product-demonstration areas highlighted Symantec's newest products. In fact, the program was so successful that the BLK MKT continues to have legs long after the 2010 show: It's now part of Symantec's Norton Truck Tour, a road show traveling to events and retail locations throughout North America on a 48-foot 18-wheeler.
By exposing the virtual world of
cybercrime and pairing it with tangible product-information activities, Symantec created a perfect one-two punch of education and soft-sell pitch. And given the BLK MKT's continued success, one thing is crystal clear - crime does pay, after all. E
|
|
|
|














 Here, staffers invited interested booth visitors to drop their business cards into a fish bowl and grab a seat in a small presentation space to watch the show, which took place several times throughout the day. Featuring a raised platform, two black director's
chairs, and a 52-inch flatscreen monitor mounted to a white back wall, the aisle-side trivia game area caught the attention of passersby, who often congregated in the aisle to enjoy the show. Before the host took the stage, he drew a name from the bowl, and that person was beckoned to take a seat on stage with him to play the game. After answering several questions about Symantec and its products, the contestant received a prize (a Nintendo Wii console, Flip camera, GPS unit, or a set of Bose headphones) based on the number of correct answers he or she provided. Those that watched the trivia game received a stamp on their passport card and were invited to visit the BLK MKT (if they hadn't yet) or head over to the product-demo areas. By either touring the BLK MKT or sitting through the game and then visiting one of the six demo stations, attendees obtained the passport stamps necessary to receive their free copy of Norton AntiVirus.
Here, staffers invited interested booth visitors to drop their business cards into a fish bowl and grab a seat in a small presentation space to watch the show, which took place several times throughout the day. Featuring a raised platform, two black director's
chairs, and a 52-inch flatscreen monitor mounted to a white back wall, the aisle-side trivia game area caught the attention of passersby, who often congregated in the aisle to enjoy the show. Before the host took the stage, he drew a name from the bowl, and that person was beckoned to take a seat on stage with him to play the game. After answering several questions about Symantec and its products, the contestant received a prize (a Nintendo Wii console, Flip camera, GPS unit, or a set of Bose headphones) based on the number of correct answers he or she provided. Those that watched the trivia game received a stamp on their passport card and were invited to visit the BLK MKT (if they hadn't yet) or head over to the product-demo areas. By either touring the BLK MKT or sitting through the game and then visiting one of the six demo stations, attendees obtained the passport stamps necessary to receive their free copy of Norton AntiVirus. 



